
It’s a cybersecurity firm’s worst nightmare. On December 8, 2020, FireEye’s CEO revealed the company had been breached by a sophisticated hacking operation — most likely carried out by a malicious actor from a well-resourced nation-state. The dust has yet to fully settle, but the impact of the breach reaches far beyond FireEye.
That’s because you might be vulnerable, too — whether you’re a FireEye customer or not.
ARE YOU AT RISK?
Here’s what happened. In short, FireEye developed a sizeable library of “red team” tools — which, effectively, were designed to test a customer’s defenses by safely attacking them. Although these tools were designed to be used as part of a safe, nondestructive assessment, they can be quite dangerous in the wrong hands. And that’s exactly where these tools are now — in the hands of bad actors who seek to use them to breach, disrupt, and steal data from a victim.
In response, FireEye has released a list of CVEs (also detailed below) to ensure everyone knows what vulnerabilities are out there — and they’re updating their products to detect them. But, regardless of your security vendor, the question still remains: “How do you know you’re safe from these recently stolen attack tools?”
HOW KEYSIGHT CAN HELP
Are you protected? Are you safe? Do you need to take remedial action? You’ve got questions — and Keysight Threat Simulator has the answers. (Our BreakingPoint security test products also provide coverage for most of these attacks, but this post focuses on Threat Simulator.)
A breach and attack simulation (BAS) tool and component of our Security Operations Suite, Threat Simulator enables you simulate attacks on your production network to see if you’re vulnerable to FireEye’s most critical CVEs (watch this space, we’ll be adding more tests soon).
And here’s the best part — you can do it for free.
Security means as much to us as it does to you. That’s why we’re offering a free, no obligation, 14-day trial of Threat Simulator. Just register here, download our easy-to-deploy agent, and log into your personal SaaS portal and run the assessments described below. Seriously — it’s that simple. And if you have any questions or need help getting started, please don’t hesitate to reach out to our Security Solutions team. We’re always happy to help!
RUNNING THE RELEVANT ASSESSMENTS IN THREAT SIMULATOR
Threat Simulator contains a robust library of assessments that are divided into three main categories: Policy, Instrumentation, and Kill-chain. Each assessment is designed to measure the security aspects of a specific zone or a function of an organization, security control, or an application. In this case, you’ll want to utilize the Nation-State Sponsored Attacks assessment. Consisting of regularly updated security audits, it focuses on exploits that are (1) based on the advisories of the United States National Security Agency (NSA) and (2) are specifically known to be leveraged by various state-sponsored actors.
Opening this assessment in Threat Simulator reveals 11 network-security audits. From this list we can clearly determine the CVEs that were associated with FireEye’s red-team toolkit breach, such as CVE-2019-11510, CVE-2020-1472, CVE-2019-0708, etc.
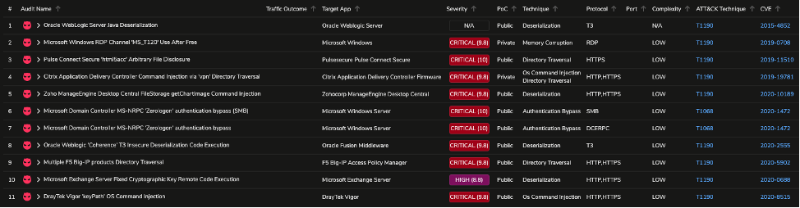
You can run this assessment in either of two simple methods:
- Have the managed Dark Cloud service emulate an external adversary with a random public IP address to target an internal system that runs a Threat Simulator agent.
- Initiate attacks internally between a pair of agents that span multiple security zones to determine lateral vulnerabilities.
To keep things simple, let’s emulate a scenario that involves an external adversary compromising the DMZ and moving laterally towards one of the branch sites such as BRANCH-1:
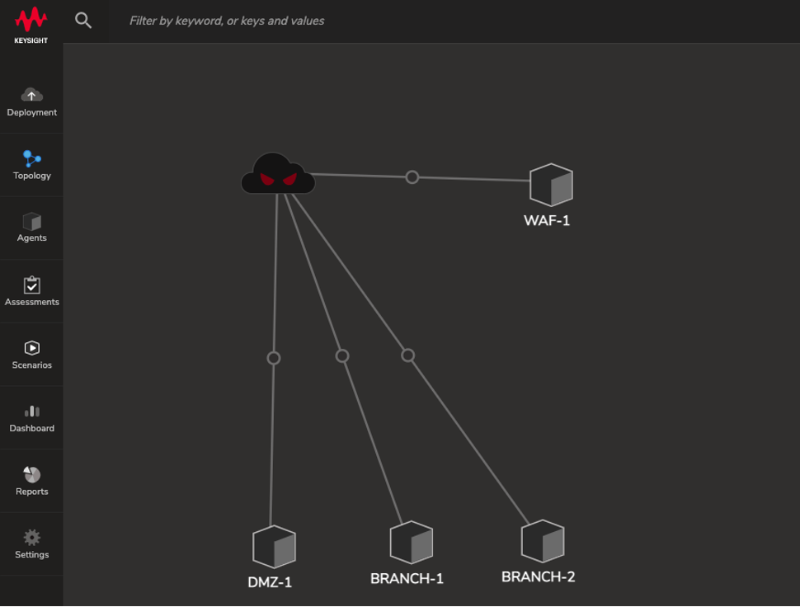
EVADING DETECTION
As opposed to utilizing static and predefined PCAPs to run an assessment, Threat Simulator instantiates the required application services to model the threat in a realistic manner — including emulating external entities, such as Command and Control servers. One of the many advantages of this architecture is that it enables you to modify attributes of the attack for an evasive approach and determine if basic inspection scanning (such as SSL DPI) is operating as intended. By toggling transports like HTTP and HTTP over SSL (HTTPS), you can easily determine if malware is hiding in plain sight!
RESULTS
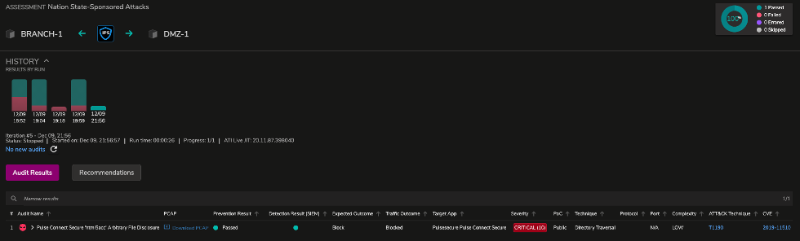
Running the assessment between DMZ-1 (demilitarized zone) and BRANCH-1 (branch site) yields the following results — assuming it’s also protected by a next-generation firewall (NGFW) with default security profiles.
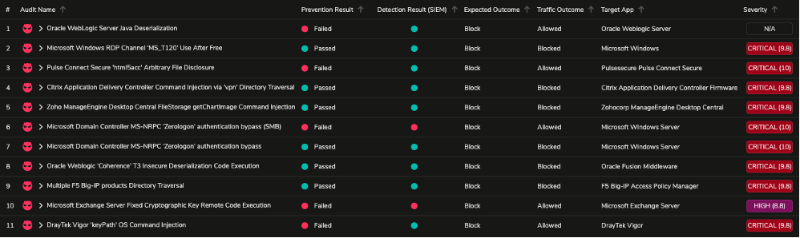
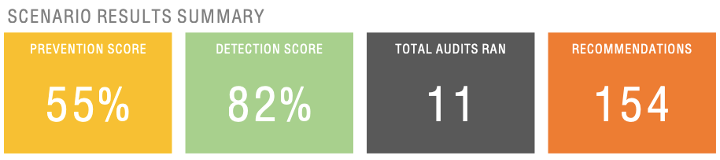
Following Threat Simulator’s recommendations and making the necessary adjustments on your NGFW yields a better result for a specific assessment such as CVE-2019-11510 — which was configured, by default, to be in “alert-only” mode. Modifying the default attribute to “reset” mode and updating the respective security policy ensures a proper prevention and detection outcome in the consecutive run.
CONTINUOUS VALIDATION
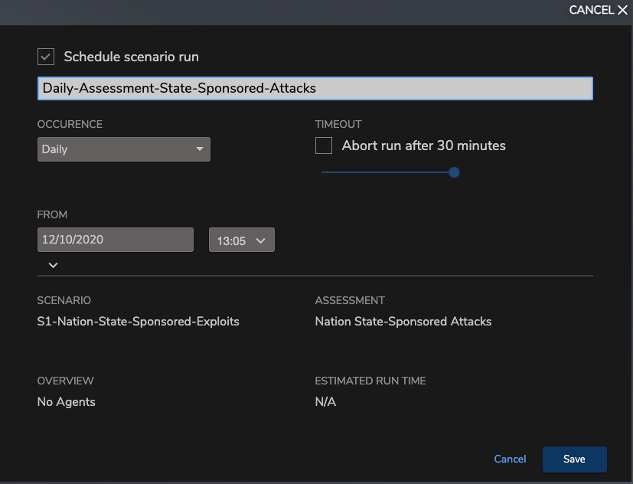
Perhaps the most substantial feature of Threat Simulator is the ability to schedule tasks to perform continuous validation in tandem with constant updates from Threat Simulator’s Application and Threat Intelligence feed. The scheduling feature makes it easy to run scheduled assessments on a periodic basis or a one-off assessment run, and continuously gather metrics on the efficacy of the security controls involved. This is a compelling alternative to one-off testing.
RELEVANT CVES
- CVE-2019-11510 – pre-auth arbitrary file reading from Pulse Secure SSL VPNs – CVSS 10.0
- CVE-2020-1472 – Microsoft Active Directory escalation of privileges – CVSS 10.0
- CVE-2018-13379 – pre-auth arbitrary file reading from Fortinet Fortigate SSL VPN – CVSS 9.8
- CVE-2018-15961 – RCE via Adobe ColdFusion (arbitrary file upload that can be used to upload a JSP web shell) – CVSS 9.8
- CVE-2019-0604 – RCE for Microsoft Sharepoint – CVSS 9.8
- CVE-2019-0708 – RCE of Windows Remote Desktop Services (RDS) – CVSS 9.8
- CVE-2019-11580 – Atlassian Crowd Remote Code Execution – CVSS 9.8
- CVE-2019-19781 – RCE of Citrix Application Delivery Controller and Citrix Gateway – CVSS 9.8
- CVE-2020-10189 – RCE for ZoHo ManageEngine Desktop Central – CVSS 9.8
- CVE-2014-1812 – Windows Local Privilege Escalation – CVSS 9.0
- CVE-2019-3398 – Confluence Authenticated Remote Code Execution – CVSS 8.8
- CVE-2020-0688 – Remote Command Execution in Microsoft Exchange – CVSS 8.8
- CVE-2016-0167 – local privilege escalation on older versions of Microsoft Windows – CVSS 7.8
- CVE-2017-11774 – RCE in Microsoft Outlook via crafted document execution (phishing) – CVSS 7.8
- CVE-2018-8581 – Microsoft Exchange Server escalation of privileges – CVSS 7.4
- CVE-2019-8394 – arbitrary pre-auth file upload to ZoHo ManageEngine ServiceDesk Plus – CVSS 6.5
DON’T GO IT ALONE
Staying secure isn’t always easy, but it’s always worth the effort. But don’t feel like you need to go it alone. If you have any questions, don’t hesitate to reach out to our Security Solutions team. Seriously. Whether you’re setting up Threat Simulator or just want some sage advice, we’re happy to help!
Happy threat hunting!
