
If you are looking for information about Log4J impact on Keysight products, please visit our Product and Solution Cyber Security page. If you are interested in how Keysight can validate your perimeter security protection from Log4J, read on.
LOG4J GO AWAY!
Over the last 72 hours or so, most of the cybersecurity world has become aware of the Log4j / Log4Shell zero-day vulnerability and its widespread impact on most web servers, cloud applications, internet appliances, and embedded devices. You can read all the gory details documented in CVE-2021-44228, but here’s the bottom line: this has the potential to be really, really bad.
So, why is everyone so worried about Log4j? In short, there are three factors combining to make this a “perfect storm” of a vulnerability:
- It affects JNDI library, which is incredibly widespread
- It’s trivial for attackers to exploit
- It enables arbitrary code execution on a target’s system
Yeah. Not fun.
We’re not trying to fully document the technical aspects of the attack here. There are plenty of sources for that online. At this moment, network and security teams are racing to mitigate the threats to their systems via a combination of updating to Log4j 2.15, the latest version of the software, and enabling screening protection on perimeter devices. Given the severity, 10 out of 10, of the vulnerability and the widespread exploitation attempts we are seeing in the wild, it’s extremely important to mitigate the threat as quickly as possible. But given the realities of holiday staffing and system uptime demands, patching may be difficult to expedite — so WAFs and Next-Gen Firewalls will be called into service as front-line protection until system vulnerabilities are directly addressed.
However, screening for Log4j attacks is decidedly nontrivial. That’s why it’s a good idea to test your protection to validate it’s working as expected while you work on system patching. We can help with that — and it won’t cost you a dime. Details on that below.
WHAT OUR HONEYPOTS ARE SHOWING US
Let’s take a look at what we’ve observed of the attack directly. Keysight operates a global honeypot network, which we use to track the various malware and other attacks hackers are employing each and every day. CVE-2021-44228 was just released Friday afternoon. As you can see from the graph below, Log4j exploitation attempts against our honeypots were exploding by late Saturday.
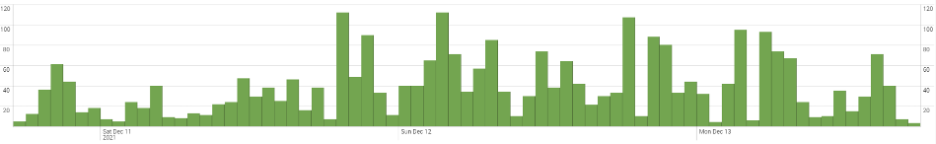
Keysight Log4j honeypot tracking
What do these attacks look like in real life? Here’s a look at some JSON logs pulled from one of our honeypots. We’ve changed the IP addresses to obscure both our IP addresses and those of the attacker, but make no mistake: this is a real attack attempt. As you can see, the attacker is trying to trick our system (not vulnerable) into fetching code from the [hostile-IP]\securityscan, which would then be executed locally. We’ve seen this attempt executed over LDAP and DNS, but other mechanisms are possible. 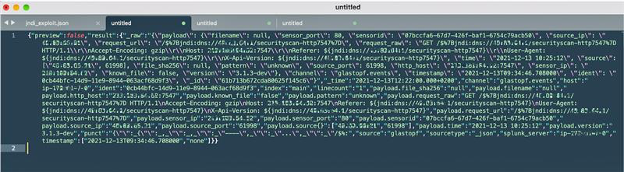
Live Log4j exploit JSON from honeypot
HOW CAN YOU PROTECT YOURSELF FROM LOG4J?
Of course, we recommend that you update your vulnerable systems as quickly as possible. However, as an immediate safeguard, it’s also quick and prudent to implement perimeter screening on your WAF, IDS/IPS, or NGFW in parallel. Due to the urgency and severity of the issue, and the exposure level so many will have, it’s also a very good idea to test your protection.
That’s why we’re offering a free Log4j vulnerability assessment via Keysight Threat Simulator. An element of Keysight’s Security Operations Suite, Threat Simulator is a breach and attack simulation tool that safely simulates attacks against your network, endpoints, email, and perimeter defense systems to highlight any areas where your protection falls short. A cloud-based SaaS product, it’s safe to use in your production network because the only actual network communication occurs between Keysight software agents. We manage the attacking agents in the cloud, and you deploy an agent in the protected segment (cloud or on-prem) as the other end of the communication.
Here’s how you can assess your Log4j protection for free — with absolutely zero obligations:
- Sign up for a Free Trial which gives you 2 agents for up to 14 days (no credit card needed). If you are in Europe, you might prefer our trial hosted in the EU.
- Download and install the small-footprint agents in your chosen environment (AWS, AZURE, Linux, Windows). Click the appropriate link for the install guide.
Select the appropriate installation guide for your environment
3. As soon as you’ve installed them, the agents will register themselves and you’re ready to go. If your agent is behind a Web Application Firewall (likely in this case), then you will need some additional agent configuration.
Agent configuration
4. Now you need to select the assessment you wish to run. There are thousands to choose from, but you’re probably going to want to focus on Log4Shell. So, in this case, you’ll want to use the supplied Apache Log4J JindiManager JINDI Injection RCE. 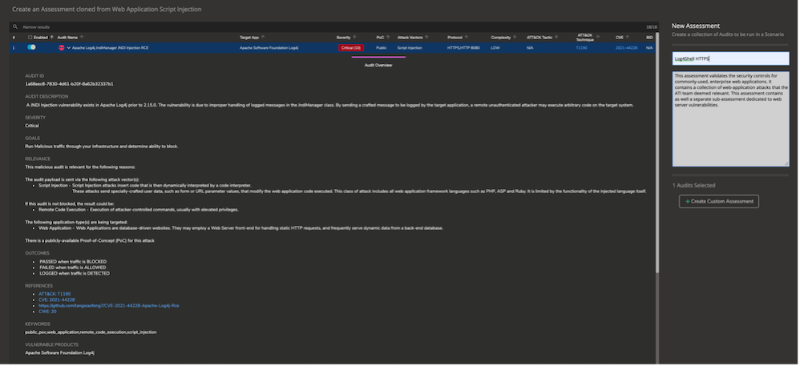
Select the Log4J assessment for this exercise
5. Now all you need to do is select which agent you wish to run the assessment against, give the scenario a name, and…
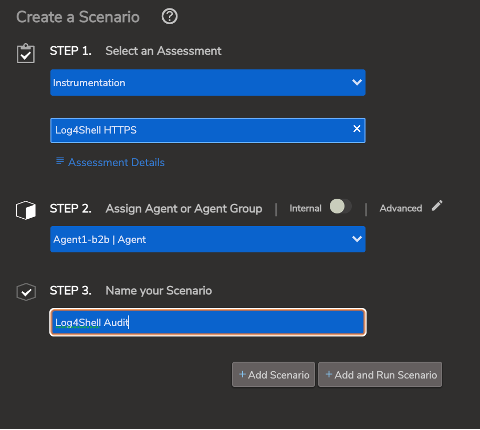
Create and name your assessment scenario
6. Run the scenario.
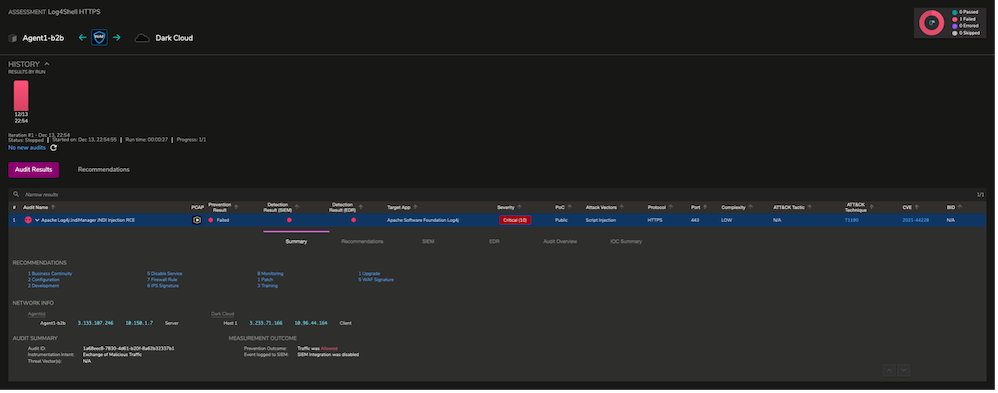 Run the scenario
Run the scenario
7. In the case it fails, meaning we didn’t block it, then we are going to want to read and implement the remediation recommendations.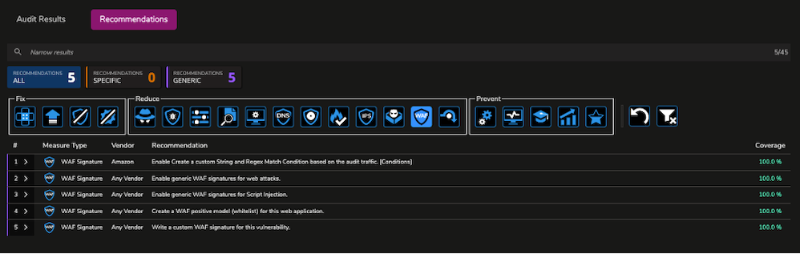
Remediation instructions are provided if an assessment fails
STAY TUNED…
Of course, the bad guys never stop changing tactics. That’s why it’s our job to stay a step ahead of them. We’ll be tracking variants as they evolve over time, so as soon as something changes, you’ll be the first to know.
Be sure to watch this space for future updates, and don’t hesitate to reach out if you have any questions — we’re always happy to help you stay protected!
