Financials 2024
Data and Information 2024
From Data Overload to Unified Insights with Grafana and ADAPTERA
We are excited to announce a strategic partnership with Grafana, an APM and Observability visionary according to the Gartner 2023 Magic Quadrant, and the leading open source visualization platform. Together, [...]
Financials 2023
Data and Information 2023
Financials 2022
Financial Statements 2022 Data and Information 2022
Event: Defending IT and OT in the age of IoT and Cloud
Join us for an evening dedicated to modern OT cyber security protection. Witness how we can help you deploy best-of-breed OT and IIoT protection, while also strengthening your enterprise-wide cyber [...]
Infographic: Why securing OT is core to guarding your business
Microsoft Defender for IoT is a unified security solution built specifically to identify IoT and OT devices, vulnerabilities, and threats. Download our infographic to see why securing your OT is [...]
Join us for the webinar: Built for today’s IT agility → SolarWinds Hybrid Cloud Observability
ADAPTERA, your Observability Expert Partner, invites you to join our webinar to explore the full potential of SolarWinds®️ Hybrid Cloud Observability. SolarWinds®️ Hybrid Cloud Observability offers organizations of all sizes [...]
Join NetBrain at CISCO Live!
Be prepared. Cisco Live is on Feb 6-10 Visit NetBrain in Booth E03 and see for yourself 👇👇👇 🛑 Network Automation for Outage Prevention 🩺 Network Automation for Automated [...]
Making the most of your Kubernetes applications: Learn how at Ignite by Akamas
Unlock the full potential of your Kubernetes applications. Join our upcoming Ignite by Akamas event on January 25 at 19:30 EET to learn how to achieve double-digit cloud cost [...]
Invest your unspent 2022 budgets in observability
As the end of year approaches, financial pressures are driving teams to make the most of their unspent budget. ADAPTERA, your expert partner for observability, provides [...]
New Release 11 Aligns NetOps to Business
Prevent Outages Automatically Release 11 dramatically lowers your operational costs by automating the operation of your network throughout its lifespan. It starts with the automatic creation of network [...]
Next generation AIOps with IBM
We welcome you to a brief introduction of the overall IBM AIOps portfolio and targeted presentation of Instana, Turbonomic, and Watson for AIOps. And discuss your question with engineers [...]
How Ease of Use Impacts Network Visibility
A fundamental question for network visibility solutions almost always involves the following, “How can you improve the short term and long-term operating costs for your monitoring [...]
Network Visibility Architecture for the Hybrid, Multi-Cloud Enterprise
This summary of Enterprise Management Associates (EMA) research explores how IT and security organizations use network visibility architectures to deliver network packets to critical performance and [...]
Juice IT up with AIOps!
We are delighted to invite you to attend the “Juice IT up with AIOps” face to face event, organized by Performance Technologies, where ADAPTERA will present how we can [...]
Traffic Intelligence for Government & Public Sector
The Allot Traffic Intelligence solution for the public sector assures an excellent Digital Experience and the delivery of online services to the public, as well as mission-critical applications [...]
Network Application and Security Test Newsletter
CyPerf Continues to Transform Application and Security Testing Keysight's CyPerf, a subscription based cloud-native application and security test solution deploys light-weight test agents across a variety of physical, cloud, [...]
3 Steps to Securing Your Healthcare Network
The Threat Is Real – The Time Is Now Geopolitical uncertainty has dramatically increased the chances that healthcare organizations will experience more security attacks in the next [...]
NetBrain takes the WORK out of Network
Ever wish you could take the "work" out of "network"? We get it, being a network engineer in today's complex network environments isn't easy, to say the [...]
CyPerf Continues to Transform Application and Security Testing
If you’ve heard about Keysight CyPerf, I hope you will enjoy the updates that I share below! If you have not heard about CyPerf, it might be [...]
ADAPTERA – Microsoft Defender for IoT
Η ADAPTERA, Gold Microsoft Partner, παρέχει μοναδικές Microsoft λύσεις κυβερνοασφάλειας για κρίσιμες υποδομές OT/ICS. Η επιλογή του Microsoft Defender for IoT διασφαλίζει την πλέον καινοτόμα και αποτελεσματική πρόταση [...]
ADAPTERA – Gold Microsoft Partner
We’re excited to announce that ADAPTERA has met all the requirements to achieve Gold Cloud Platform competency, validating readiness to deliver solutions and services based on Microsoft’s cloud platform. Joining [...]
Versa Enterprise Video
The Enterprise IT landscape has evolved rapidly with increased importance of the cloud and Software-as-a-Service (SaaS). Learn how to prepare your Enterprise for digital transformation by watching [...]
Traffic Intelligence and Digital Experience Monitoring Solutions
For Small, Medium and Large Enterprises Now more than ever, an excellent Digital Experience is critical for you as you strive to maintain your business resilience. Whether you are a [...]
VMWARE smart assurance
Automated Service Assurance for Virtual and Physical Networks AT A GLANCE Proven, carrier-scale network and digital infrastructure management for today’s and tomorrow’s CSP networks • Holistically monitor and [...]
Managing CLOUD CONNECTIVITY with NetBrain
Traditional network operations tools don't provide sufficient visibility to the cloud, resulting in silos for Amazon AWS, Microsoft Azure and Google cloud. But NetBrain's "dynamic map" technology offers the [...]
Why Internal Network Security Monitoring (‘INSM’) Begins with Visibility
The concept of visibility was introduced to most of us at an early age. The message was clear. Seeing is important. Watch where you’re going! Steer clear [...]
How Can I Reduce Network Security Risk – Part 1
Step 1 – Reduce as many vulnerabilities within the network as possible I recently wrote a blog Find Your Security Vulnerability Before Hackers Find It For You and I [...]
Optimizing your Kubernetes clusters without breaking the bank
Organizations across the world are fast adopting Kubernetes. That is because Kubernetes provides several benefits from a performance perspective. Its ability to densely schedule containers into the underlying [...]
Find Your Security Vulnerability Before Hackers Find It For You
Every Network Has A Security Vulnerability - Where Is Yours? One of the top questions on the minds of network security personnel is "how do I reduce [...]
Traffic Intelligence for the Financial Services industry
The Allot Traffic Intelligence solution provides the critical network visibility that Financial Service organizations require. It aligns application performance with business priorities, ensuring that critical financial services get [...]
How Microsoft Defender for IoT can secure your IoT devices
Cybersecurity threats are always evolving, and today we’re seeing a new wave of advanced attacks specifically targeting IoT devices used in enterprise environments as well as operational technology (OT) devices [...]
The Ultimate Guide To Building An Outlier Detection System
Part I - Design Principles In this three-part series, learn the essentials for machine learning anomaly detection for business applications. Download "Part I - Design Principles" for an [...]
Excuse me, Do you know the time?
Whilst working on a new product that we have recently launched I’ve spent quite a lot of time speaking to customers about Timing and specifically understanding how [...]
We’re Changing the World of Network Operations Forever!
Dear Partner, For 25 years, Network Operations has focused on network management from the bottom-up, device by device. That's why hybrid networks seem so complex to so [...]
Six Tests You Need Now for Distributed, Elastic Cloud Networking
Network equipment manufacturers (NEMs) are innovating to deliver solutions required to build multi-cloud networks. In this eBook you’ll learn about six key test requirements and test solutions [...]
Proactive Threat Simulation to test your cyber defenses
Cybersecurity is rightfully a top concern for Enterprises and getting more so with all the high-profile breaches making the news. Leaders don’t want their company making the [...]
Four tips to ensure optimal SD-WAN performance
While the adoption of SD-WAN brings significant cost-savings and flexibility to the enterprise, it is also a significant operational transformation—one that requires greater attention to performance monitoring. [...]
ADAPTERA SNEAK Peek: Jan 19th 4PM
Please join us for our next Meetup on January 19th 2022, at 4PM, as we show a sneak peek inside the development process as Nagios gets [...]
Log4J / Log4Shell: Is Your Network Safe? Find Out for Free with Keysight
If you are looking for information about Log4J impact on Keysight products, please visit our Product and Solution Cyber Security page. If you are interested in how Keysight can [...]
Bypass Switches – “Quis custodiet ipsos custodes?”
For those of you who skipped high school Latin, a close translation would be – "Who will guard the guards?" It's a very valid question in situations [...]
Threat Detection and Response in Azure Environments
For years now, Network Detection and Response (NDR) has been in use for on-premise enterprise environments, and many consider NDR the gold standard for detecting anomalies and [...]
Subscriber-Aware Session Monitoring: The ABCs of Network Visibility
This blog is another in a series devoted to exploring critical aspects of network visibility. The topic this time relates to how service providers can use network [...]
Change Management Automation
NetBrain Automation includes powerful Change Management Automation which enables teams to reduce the risks and costs associated with network change processes. Leveraging NetBrain’s Runbook Automation, teams can deploy [...]
The Future of Network Operations
According to analyst firm Enterprise Management Associates (EMA) research, today’s enterprise network manager is being asked to be a strategic business partner, not just a firefighter. But when [...]
ADAPTERA – Αναβάθμιση επιπέδου συνεργασίας με ZABBIX
Η ADAPTERA είναι ο εξειδικευμένος συνεργάτης των μεγαλύτερων οργανισμών στην Ελλάδα, για παροχή λύσεων Total Visibility ως βάση για την εξασφάλιση & βελτιστοποίηση της απόδοσης, την μείωση κόστους [...]
Keysight Unveils Industrial Visibility Solutions for Electric Utility Market
Keysight Technologies, Inc. (NYSE: KEYS), a leading technology company that delivers advanced design and validation solutions to help accelerate innovation to connect and secure the world, announced a new [...]
Network Detection and Response: Active risk management prevents ransom attacks
Network Detection and Response: Active risk management prevents ransom attacks Thursday, October 7th @ 13:00 How to gain full control over network performance and security using [...]
What is Supply Chain Security and What it Means to Critical Infrastructure ICS/OT
What is Supply Chain Security and What it Means to Critical Infrastructure ICS/OT What is Supply Chain? Supply Chain describes the entire process of producing [...]
Network Detection and Response: Active risk management prevents ransom attacks
Network Detection and Response: Active risk management prevents ransom attacks Thursday, October 7th @ 13:00 How to gain full control over network performance and security using [...]
What the ‘Must Be This Tall to Ride Sign’ says about Cybersecurity and Critical Infrastructure
When asked to summarize into 7 words or less, the National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems (‘NSM’)- yes, the memo you can’t even [...]
Imply is a full stack, multi-cloud data platform
Why use Imply?Imply provides a suite of tools to simply, safely, and efficiently run large scale analytic workloads.Simple operationsMinimize operational complexity while ensuring high performance, constant uptime, [...]
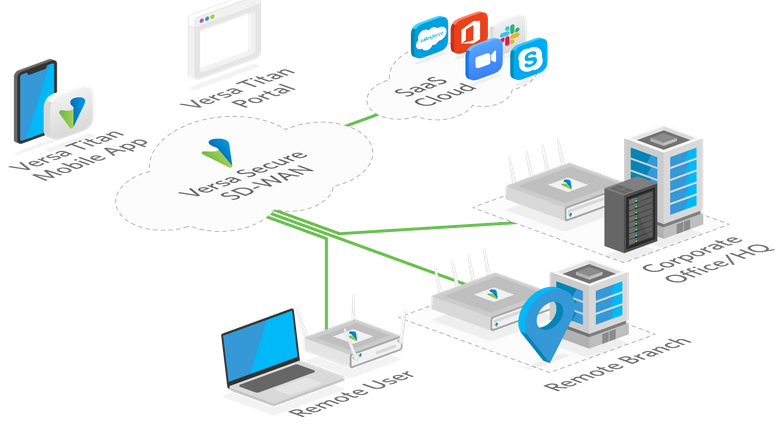
Versa Titan: SASE for Lean IT
Cloud-Managed Networking and Security, Simplified. Versa Titan delivers SASE with advanced application intelligence managed from the cloud, making it easier for IT to manage and secure their [...]
What Is Breach And Attack Simulation? Watch This Video!
When it comes to network security, your best defense is a good offense. You've outfitted your network with a diverse array of network security tools, and your [...]
Enterprise DDoS Protection
Safeguard your network and your business from costly disruption or downtime caused by DDoS attacks Protect your network from small and large volumetric DDoS attacks, as well as [...]
Webinar: Validate SDWAN/SASE network security for the post-pandemic world with Keysight Cyperf
Dear Partner, The pandemic WFH era fueled a dramatic shift to edge networking using technologies like SASE, SD-WAN, and cloud. With all the changes in the network, [...]
Assure the performance of your important applications
A variety of different applications are running on your network. They serve different purposes, should be handled differently, and some shouldn’t even be on your network. Application control [...]
Top Digital Transformation Challenges for Enterprise Networks
Is your network ready for digital transformation? Managing a highly complex network infrastructure is nowadays harder than ever. NetOps teams have been tasked with an enormous number of challenges: From solving [...]
Digital Twins: What Do They Enable for Your Organization?
You’ve heard the phrase, digital twin. But what is a digital twin really for? Chris Lee, Customer Success Manager, Falkonry explains the trend behind the technology and for some important [...]
Tinkoff Adopts Anodot’s Next-Level Technology to Revolutionize its Customer Experience, Payment, and Trading Monitoring
Anodot enables financial services giant Tinkoff to provide operational efficiency across its platform reducing time to detection by 30% ASHBURN, Va.--(BUSINESS WIRE)--Today, Russia’s leading fintech innovator, Tinkoff, announced that [...]
Understanding Load Balancing Essentials
In this post we’ll review some of the essential ideas in Load Balancing to help you understand how to get the best configuration for your application. Load balancing [...]
Add-on Modules
NetBrain’s core dynamic mapping and runbook automation capabilities can be augmented with add-on modules. NetBrain’s Change Management Module helps teams deploy network changes faster and more safely. The [...]
Best Practices and Use Cases for Network Visibility
Network visibility enables IT teams to quickly isolate security threats and resolve performance issues. This white paper provides examples of how to tighten security, reduce costs, accelerate troubleshooting, [...]
Extending Automated Network Operations to Multi-Cloud Environments
Today’s enterprise networks are Frankenstein’s monsters of different network technologies– multi-cloud, traditional, virtual, and software-defined – from dozens of vendors that support applications and users across the [...]
Validating containerization – What was small has become smaller, yet larger.
Let me explain this confusing headline. When virtualization became popular, users were amazed by the flexibility it provided. We were able to segment large hardware into several small [...]
NIS Directive for Critical Infrastructures – Secure your enterprise ICS/OT environments with Microsoft Defender for IoT
Αγαπητοί Συνεργάτες, Η αυξανόμενη σφοδρότητα και συχνότητα των εξειδικευμένων κυβερνοεπιθέσεων σε λειτουργίες και εγκαταστάσεις κρίσιμων υποδομών μέσω των ΙΤ & ΟΤ δικτύων, αποτελεί έκκληση για δράση προς τις [...]
Live Webinar: Automate & Accelerate Network Operations
Join Our Webinar to See What’s New Automation is a major focus for enterprises looking to improve IT workflows, especially when facing 1,000s of tickets daily. But today’s [...]
The Road to Zero Touch Goes Through Machine Learning
The telecom industry is in the midst of a massive shift to new service offerings enabled by 5G and edge computing technologies. With this digital transformation, networks and network services are [...]
5 Network Security Trends to Watch in 2021
It is not only the COVID-19 pandemic and the associated rise of remote work that is shaping the everyday routine of network security practitioners. Let's take a look [...]
A Network Architect’s Guide to Inline Security – Performance Matters
Inline security solutions operate more efficiently, troubleshoot faster, and stay online longer with the right inline security architecture. Get the details you need to make the best network [...]
Gartner Market Guide for Service Orchestration and Automation Platforms (SOAP)
“Through 2024, 80% of organizations using workload automation tools will switch to service orchestration and automation platforms to orchestrate cloud-based workloads.” - Gartner According to Gartner, workload automation [...]
Versa Titan: SASE for Lean IT
Cloud-Managed Networking and Security, Simplified. Versa Titan delivers SASE with advanced application intelligence managed from the cloud, making it easier for IT to manage and secure their branch [...]
2020 Report: The Greatest Cyber Threats Your Users Face
Dear Partner, Join our experts for the LIVE webinar: 2020 Cyber Threat Report: What Poses the Greatest Danger to Your Subscribers? on March 2, 2021. In 2020, European CSPs [...]
Visibility & Automation for your Hybrid Network! ADAPTERA featuring NetBrain’s Network Automation Platform
Αγαπητοί συνεργάτες, H ADAPTERA στο πλαίσιο της συνεργασίας της με τη NetBrain σας προσκαλεί στο διαδικτυακό σεμινάριο: Visibility & Automation for your Hybrid Network! ADAPTERA featuring NetBrain’s Network [...]
Top 10 Challenges Addressed with NetBrain Automation
So what does NetBrain automation actually do? How does its automation help with the hundreds of tasks you face every day? Here are 10 common challenges that NetBrain [...]
IT PRO | DEV Connections 2020
Αγαπητοί συνάδελφοι και φίλοι, Το IT PRO | DEV Connections 2020 επιστρέφει και φυσικά δεν θα μπορούσαμε να μην είμαστε εκεί! Περήφανος SPONSOR Σας καλούμε να συμμετάσχετε [...]
Enhance and Automate Your Cybersecurity Operations
ADAPTERA invites you to a special web event, aiming to provide insights on how to enhance and automate your SecOps. Register today to watch our partners Keysight and [...]
How Network Automation Optimizes a Typical NetOps Workflow
Automation is being applied across just about every aspect of IT operations to increase speed and efficiency, improve availability, and foster agility and innovation. One area where automation [...]
RIVERBED GLOBAL USER CONFERENCE 2020
Η Riverbed διοργανώνει το Παγκόσμιο ��υνέδριο της, στις 17 Νοεμβρίου 2020, 10:00 ώρα Ελλάδος και θα μας χαροποιούσε ιδιαίτερα η συμμετοχή σας σε αυτό. Το φετινό virtual one [...]
Threat Simulator: Tuning Azure WAF Rules
Web Application Firewalls protect your web, mobile, and API applications from being exploited and are instrumental in preventing data breaches. This video demonstrates how you can use a [...]
ADAPTERA και CYBERX συνεργάζονται για την παροχή λύσεων κυβερνοασφάλειας κρίσιμων υποδομών ΟT/ICS
Η νέα ψηφιακή εποχή στις επιχειρήσεις, καθώς και η ανάπτυξη του Βιομηχανικού Διαδικτύου των Πραγμάτων ( ΙΙοΤ), φέρνουν κοντά τα ΙΤ δίκτυα των επιχειρήσεων με την ΟΤ τεχνολογία. Έτσι, [...]
NetBrain’s Network Data Model and the Foundation for Automation
IT’s Big Data When IT problems strike, the key to prompt resolution is hiding in the data – data produced when the fault occurs, historical data, and live [...]
Maximizing Application Uptime with Network Automation
Networks exist to serve the applications that run across them. As network complexity increases (think SDN and public cloud), NetOps teams must quickly determine if it’s the network [...]
[SANS Webinar] Securing Building Automation & Data Centers with OT Security Monitoring
Η ADAPTERA ως συνεργάτης της CYBERX σας προσκαλεί στο παρακάτω webinar με θέμα: "Securing Building Automation & Data Centers with OT Security Monitoring" Κάντε εγγραφή εδώ [...]
Simple and reliable network security for SMBs
When it comes to cybersecurity, what’s the difference between SMBs and large enterprises? If you guessed that the difference is related to the number of cyberattacks, then you’d [...]
DON’T JUST MAKE FASTER CHANGES, MAKE SAFER CHANGES
Define changes interactively Reduce design review from weeks to days. Model and visualize everything on a Dynamic Map — no more untangling a bunch of text to understand [...]
Allot Traffic Intelligence and Assurance Platform
Gain Visibility and Control over your applications and network, with a low TCO Whether you are a small business with no IT expertise, a growing mid-size business, or [...]
ADAPTERA – NEA ΣΥΝΕΡΓΑΣΙΑ ΜΕ CYBERX
Η ADAPTERA υπέγραψε επίσημη συνεργασία για την Ελλάδα και την Κύπρο με την CYBERX, παγκόσμιο ηγέτη στον χώρο του IoT/OT Security. Η ADAPTERA διαθέτει ισχυρή εξειδίκευση και εκτενή [...]
Top 4 Reasons to Optimize Your SD-WAN
I often get the question “When should I enable WAN optimization with my SD-WAN?” It’s a good question, especially since it is a common mistake to either conflate [...]
MPLS is Obsolete
Is it? Is MPLS fast approaching its demise as it is portrayed in many industry articles and blogs? I beg to differ. For the foreseeable future, I do not [...]
FireEye Breach: Why You Could Be At Risk and How Keysight Can Help
It’s a cybersecurity firm’s worst nightmare. On December 8, 2020, FireEye’s CEO revealed the company had been breached by a sophisticated hacking operation — most likely carried out by [...]
Network Virtualization – Are 3rd party Network Visibility Solutions still relevant?
You may or may not be familiar with network virtualization, so let me give a very high-level definition of what it is. Virtualization started with server virtualization, it [...]
Not everything is always as it seems..
There are many things that at first glance look the same. They may have the same primary function or provide you with the same service, but when you [...]
Data Center Visibility – Go Big or Stay Blind
One of my coworkers, Guang Zhang, who is one of those quiet, smart, thoughtful people (more or less the opposite of your humble narrator), spent a fair amount [...]
Reduce the cost of tool sprawl with smarter network monitoring
Monitoring tools have always been critical for ensuring network performance and security. Top vendors have designed new tools specifically for monitoring networks with virtualization, cloud infrastructure, distributed data [...]
Azure Defender for IoT including CyberX
Learn how Azure Defender for IoT incorporates CyberX technology to deliver agentless security for unmanaged industrial IoT devices in Operational Technology (OT) networks, including asset discovery, vulnerability management, [...]
Versa Networks for Enterprises
With Versa, you get carrier-grade solutions and virtualized branch security for a software-defined enterprise all while reducing costs and increasing performance.
Azure Defender for IoT: Agentless Security for OT
Summary Azure Defender for IoT delivers agentless security for continuously monitoring Operational Technology (OT) devices in industrial and critical infrastructure networks. Incorporating IoT/OT-aware behavioral analytics from Microsoft's recent acquisition [...]
Discover and Remediate Security Gaps – Safely
Watch this 3-minute video to see how Threat Simulator, our BAS platform, enables you to: · simulate real-world attacks without compromising applications · discover gaps and vulnerabilities in security configurations [...]
Out-of-Band Monitoring Solutions
Visibility powered by a multi-layer security fabric improves enterprise network monitoring performance. Intelligent network visibility allows IT to strengthen network security, reduce monitoring costs, increase return on investment [...]
Tech TIPS With Packet Boi
Τι είναι το Network Packet Broker (NPB); Ίσως να είναι το πιο σημαντικό εργαλείο στο #datacenter σας! Ανακαλύψτε τι κάνει ένα NPB και γιατί είναι τόσο χρήσιμο για [...]
Filtering, Deduplication and Other Cost Containment Tricks
Amazing Things You Can Do with a Network Packet Broker As networks grow and become increasingly complex, the cost to run and maintain them increases. However, Network packet [...]
How Flowmon Helps to Detect SUNBURST Trojan Attack in Your Network
Flowmon Anomaly Detection System from Kemp now contains Indicators of Compromise (IoC) for the SUNBURST trojan specifically. Users of the Flowmon network detection and response (NDR) tool [...]
Digital Banking and Financial Network Solutions
The financial industry is at the forefront of network technology. The reality is that the financial sector — from retail banking to high-speed trading — is at the [...]
De-duplication: The ABCs of Network Visibility
Duplicate packets of monitoring data can come from several sources, including the use of SPAN ports and the geographic location of data captures. For instance, a normally configured [...]
How to Create Actionable IoT & ICS Security Dashboards for Management & Auditors
Over the last several years, boards and management teams have started to take a greater interest in IoT/ICS cybersecurity. As reports of high profile IoT/ICS attacks and breaches becoming [...]
Finding Threats, Exposing Problems
The Critical Role of Taps and Network Packet Brokers Virtualization, rogue IT, bring your own device (BYOD), and other factors are making it harder than ever to see [...]
How Keysight is Innovating in Unexpected Ways to Help Customers Secure their Organizations
Keysight continues to support customers by sharing our expertise and developing products that help solve real-world problems. Cybersecurity issues such as ransomware, malware, and DDoS attacks continue to weigh [...]
Covid-19 & the new telecom reality: traffic management more important than ever
Communication Service Providers (CSPs) are seeing a dramatically increased load on networks as more people each day work from home. With a growing number of employees and businesses [...]
Stronger Security with Network Packet Brokers
Securing a network requires more than just a menagerie of security tools. You have to ensure that your tools have effective visibility into your network and the traffic [...]
Data center management: best practices for attracting enterprise clients
Data centers are critical facilities that house computers, storage, and systems, which are all crucial for the daily operation of any modern business. There is currently a trend [...]
Threat Simulator: Breach And Attack Simulation
Continuously Validate Your cyber Defenses Security is never static. New cyber attacks, misconfigurations, and security products are rampant. How do you take control of an ever-changing threat landscape? [...]
What is Workload Automation (WLA)—and How is it Changing?
Why Workload Automation is the best way to schedule and manage tasks related to business processes and transactions. Some call it job scheduling. Some still call it batch processing. Although [...]
CyberX releases 2020 Global IoT/ICS Risk Report
October 22, 2019 - CyberX, the IoT and industrial control system (ICS) security company, announced the availability of its “2020 Global IoT/ICS Risk Report.” The data illustrates that [...]
Cloud Orchestration and Automation Explained
Cloud orchestration has become a critical part of the multi-cloud and hybrid IT infrastructure for most major enterprises. But being in the cloud does not simply mean storing [...]
Data Supply Chain: Application Automation for OpenShift
This solution paper describes how Stonebranch supports seamless application migration and modernization to orchestrate data supply chains. Discover how Stonebranch has simplified the migration and modernization of applications deployed [...]
Workload Automation for Hybrid Cloud Management
With Hybrid Cloud environments becoming increasingly popular, IT Ops professionals are leveraging Workload Automation solutions to support their Hybrid IT strategies. IT Ops professionals have long used Workload [...]
Network Traffic Congestion Solutions and Management
When it comes to maintaining a high QoE, the biggest issue for service providers is providing enough capacity to meet bandwidth demand. But keeping up with the ever-increasing volume [...]
Avoid These App Migration Pitfalls When Moving to the Cloud
It’s well established by now that businesses are looking to the cloud to help secure sustainable advantages over competitors. But in today’s digital world, technical and business leaders [...]
Hawkeye + Office 365: Maintain Peak Performance Across All Your Microsoft Apps
SaaS applications like Office 365 offer increased flexibility, scalability, and cost effectiveness. However, as services and data migrate outside your network perimeter, performance can suffer. And when infrastructure [...]
Make every experience a compelling one.
When it comes to monitoring how apps perform for your users, guesswork doesn’t work. Estimating what your end users are experiencing is inefficient, inaccurate—and often costly. With Riverbed, [...]
Security Monitoring of Critical Infrastructure
Security breaches continue to remain a persistent challenge for both data center providers and enterprises monitoring their networks, even as the expenditures on network security appliances increases. When [...]
In the Age of SaaS, Many Lessons Can be Leveraged from the Past
With the recent announcement of the Riverbed SaaS Accelerator service it gives us pause to really consider where we have been, where we are today in a digital age [...]
New practices explained in ABCs of Performance Monitoring
Ixia has published a new e-book called The ABCs of Performance Monitoring. This book is a reference guide for those who want to learn about new practices for monitoring application [...]
For Riverbed and Its Customers, It’s the People That Matter Most
It’s no secret that businesses and organizations around the world are in the midst of massive digital transformations. In fact, IDC expects spend on digital transformation will reach nearly [...]
Achieve Network Visibility in the Public Cloud
Organizations in every market sector are migrating to public cloud, even those not typically associated with technology. This trend is growing because of the increased flexibility and agility [...]
From Big Data Management to Cyber Hunting Security, What to Expect in 2020
In many ways, the technology topics that have been brewing for much of 2019—think big data, cyber hunting, Internet of Things (IoT), 5G, customer preferences and user experience—will [...]
Assuring Your Service Level with Ixia IxProbe
One of the most common questions I hear when I talk about SD-WAN is the idea of whether you can take a consumer or SMB-grade broadband connection and [...]
Ixia’s Guide to Visibility Use Cases – Cost Containment
As networks grow and become increasingly complex, the cost to maintain those networks increases. Learn how you can increase efficiency and reduce costs by deploying a visibility architecture that reveals where [...]
Why Are Taps Critical to Network Visibility and Security?
The first building-block to your visibility architecture is access to the data. That comes in one of two forms: a network tap or a switch port analyzer (SPAN) port [...]
The State of the Internet. Encryption-What’s Hiding in Plain Sight
In the frantic drive to encrypt, equipment makers and enterprises are finding a lack of the HTTP2.0 and TLS use data needed to properly understand and thereby handle the [...]
Five Ways to Improve Network Performance with Active Monitoring
Well-maintained infrastructure and real-time network monitoring are not always enough to keep things running smoothly and head off trouble. You need intelligence that can help you validate performance [...]
6 Facts that Will Make You Rethink End User Experience Monitoring
Consider these 6 facts as you determine how you will ensure excellent digital experience for all your users.
Multi-cloud Network Visibility
Multi-cloud is becoming the new norm. According to Dimensional Research, 74% of organizations say they use multiple cloud providers, while 43% of them have applications that span multiple cloud [...]